One of my interests is the history of computing. This blog post aims to summarise a seminar that as given by Malcolm MacCallum, University of London, held at the Open University on 30 October 2012. Malcolm used to be the director of the Heilbronn Institute for Mathematical Research, Bristol. Malcolm began by saying something about the institute, its history and its research.
This blog complements an earlier blog that I wrote to summarise a lecture that was given at City University. This earlier lecture was entitled Breaking Enigma and the legacy of Alan Turing in Code Breaking and took place back in April 2012, and was one of a series of events to celebrate the centenary of Alan Turing's birth. Malcolm's talk was similar in some respects but had different focus: there was more of an emphasis on the story that led to the development of what could be arguably one of the world's first computers.
I'm not going to say much about the historical background that is obviously connected with this post, since a lot of this can be uncovered by visiting the various links that I've given (if you're interested). Instead, I'm going to rush ahead and introduce a swathe of names, terms and concepts all of which connect with the aim of Malcolm's seminar.
Codes, Cyphers and People
In some respects the story of the Enigma code, which took place at the Government Code and Cypher School, Bletchley Park, is one that gains a lot of the historical limelight. It is easy to conflate the breaking of the Enigma code (Wikipedia), the Tunny code (Wikipedia) and the work of Alan Turing (Wikipedia). When it comes to the creating of 'the first computer' (quotes intentional), the story of the breaking of the Tunny code is arguably more important.
The Tunny code is a code generated by a device called the Lorenz cypher machine. The machine combined transmission, encryption and decryption. The Enigma code was very different. Messages encrypted using Enigma were transmitted by hand in morse code.
I'm not going to describe much of the machines since I've never seen a real one, and cryptography isn't my specialism. Malcolm informed us that each machine had 12 wheels (or rotors). Each wheel had a set of cams that were set to either 1 or 0. These wheel settings were changed every week or month (just to make things difficult). As each character is transmitted, the wheels rotate (as far as I know) and an electrical circuit is created through each rotor to create an encrypted character. The opposite happens when you decrypt: you put in an encrypted character one side and a plain text (decrypted) character magically comes out the other side.
For everything to work, the rotors for both the encrypting and decrypting machines have to have the same starting point (as otherwise everything will be gibberish). These starting points were transmitted in unencrypted plain text at the start of a transmission
Through wireless intercept stations it was possible to capture the signals that the Lorenz cypher machines were transmitting. The codebreakers at Bletchley Park were then faced with the challenge of figuring out the structure and design of a machine that they had never seen. It sounds like an impossible challenge to figure out how many rotors and wheels it used, how many states the rotors had, and what these states were.
I'll be the first to admit that the fine detail of how this was done pretty much escapes me (and, besides, I understand that some of the activities performed at Bletchley Park remains classified). What I'm really interested in is the people who played an important role in designing the physical hardware that helped with the decryption of the Tunny codes.
Depths and machines
Malcolm hinted at how the codebreakers managed to begin to gain an insight into how the Lorenz machine (and code) worked. He mentioned (and I noted) the use of depths (Wikipedia), which is where two or more messages were sent using the same key (or machine setting). Another note that I made was something called a Saltman break, which is mentioned in a book I'll reference below (which is one of those books which is certainly on my 'to read' list).
Malcolm mentioned two different sections of Bletchley Park: the Testery (named after Ralph Tester), and the Newmanry (named after Max Newman). Another character that was mentioned was Bill Tutte who applied statistical methods (again, the detail of which is totally beyond me and this presentation) to the problem of wheel setting discovery.
It was realised that key aspects of code breaking could be mechanised. Whilst Turing helped to devise the Bombe (Wikipedia) equipment that was used with the decryption of the Enigma code, another machine called the Heath Robinson (Wikipedia) was built.
One of the difficulties with the Heath Robinson was its speed. It made use of electromechanical relays which were slow, restricting the code breaking effort. A new approach was considered: the creation of a calculating machine that made use of thermionic valves (a precursor to the transistor). Valves were perceived to be unreliable but it was realised that if they were continually powered up they were not stressed.
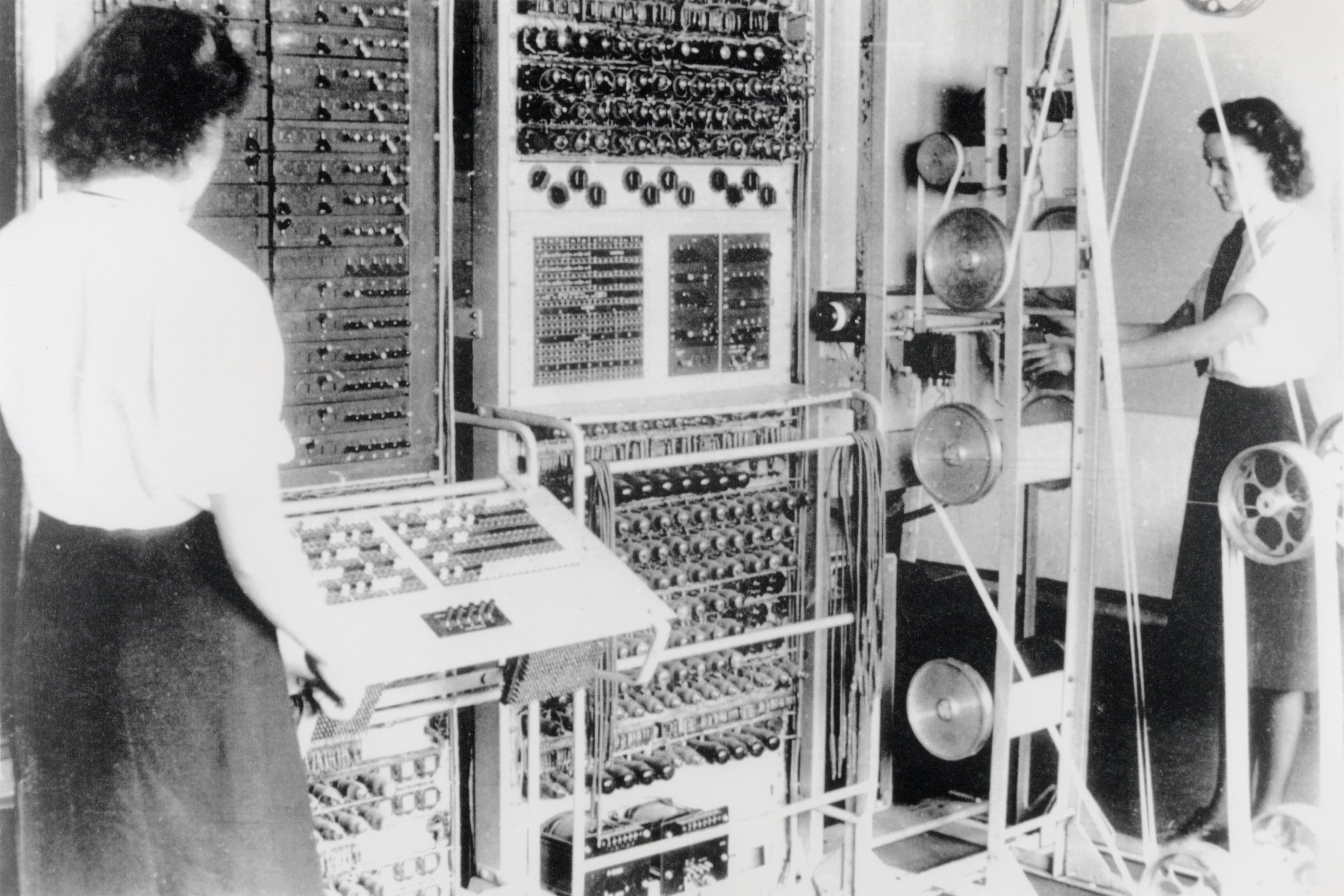
Colossus
Tommy Flowers (Wikipedia) engineered and designed a computer called Colossus (Wikipedia), drawing experience gained working at the Dollis Hill Post Office research station in North London.
Although Colossus has elements of a modern computer it could be perhaps best described as a 'special purpose cryptographic device'. It was not programmable in the same way that a modern computer has become (this is a development that comes later), but its programs could be altered; perhaps by changing its circuitry (I don't yet know how this would work). It did, however, made use of familiar concepts such as interrupts, it synchronised its operation by a clock-pulse, stored data in memory, used shift registers and did some parallel processing. Flowers also apparently introduced the term 'arithmetic and logic unit'.
Colossus was first used to break a message on 5 February 1944. A rather different valve based calculator, the ENIAC (Wikipedia), built by the Moore School of Electrical Engineering, University of Pennsylvania, was used two years later.
Final points
Malcolm told us that ten Collosi were built (I might have spelt that wrong, but what I do know is that Collosus-es certainly isn't the right spelling!), with the last one being dismantled in 1960. A total of twenty seven thousand messages were collected, of which thirteen thousand messages were decrypted. Malcolm also said that Flowers was 'grossly under rewarded' for his imaginative and innovative work on Colossus. I totally agree.
Research into the Colossus was carried out by Brian Randell from the Univerisity of Newcastle in the 1970s. A general report on the Tunny code was only recently released in 2000. Other sources of information that Malcolm mentioned was a book about the Colossus by Jack Copeland (Wikipedia) (which is certainly on my 'to read' list), and a biography of Alan Turing by Andew Hodges (Wikipedia).
Malcom's talk reminded me of how much computing history is, quite literally, on our doorstep. I regularly pass Bletchley on the way to the Open University campus at Milton Keynes. There are, of course, so many other places that are close by that have played an important role in the history of computing. Although I've already been twice to Bletchley Park, I'm definitely going to go again and take a longer look at the various exhibits.
(Picture: Wikipedia)